The state of hardware security
You can’t build anything big and important without a solid foundation. In security, hardware acts as that unyielding foundation, the basis for all other defenses. While fancy encryption and zero-trust principles can safeguard data in an environment where software is inherently untrusted, they ultimately rely on hardware’s immutable security properties. Companies are partnering with cloud providers to store their data on the same infrastructure as their competitors, so it’s not enough to know software security.
Hardware-based security measures, such as secure boot, trusted platform modules, and memory encryption, establish an initial trust anchor that software cannot easily subvert and that users can evaluate and decide to trust. This foundational layer verifies the integrity of the system before any software is executed, ensuring that the subsequent layers of security are built on a trusted base. Without this hardware root of trust, even the most robust software security mechanisms are vulnerable to low-level attacks that can compromise the entire system.
One thought experiment to understand the critical nature of hardware security is the ability to observe or spoof the user interface. At some level data have to leave the system unencrypted through a display and if the last mile of hardware isn’t secure, an attacker can have the same effects as a full system compromise.
Over the past decade, hardware security has evolved from pioneering isolated execution environments to mature, commercially deployed solutions that underpin today’s cloud and edge infrastructures. Early in the 2010s, initiatives like Intel SGX and AMD’s initial forays into secure encrypted virtualization laid the groundwork for establishing a hardware root of trust—ensuring that critical operations could run in protected enclaves even in hostile software environments. Building on these foundations, AMD introduced SEV (Secure Encrypted Virtualization) in 2016 to encrypt VM memory, followed by SEV-ES in 2017 to extend that protection to CPU register states. More recently, with the advent of SEV-SNP (Secure Nested Paging) around 2020 and Intel TDX emerging in the last couple of years, the focus has shifted from merely encrypting data to providing robust integrity guarantees that protect against sophisticated attacks like memory replay, remapping, and side channels.
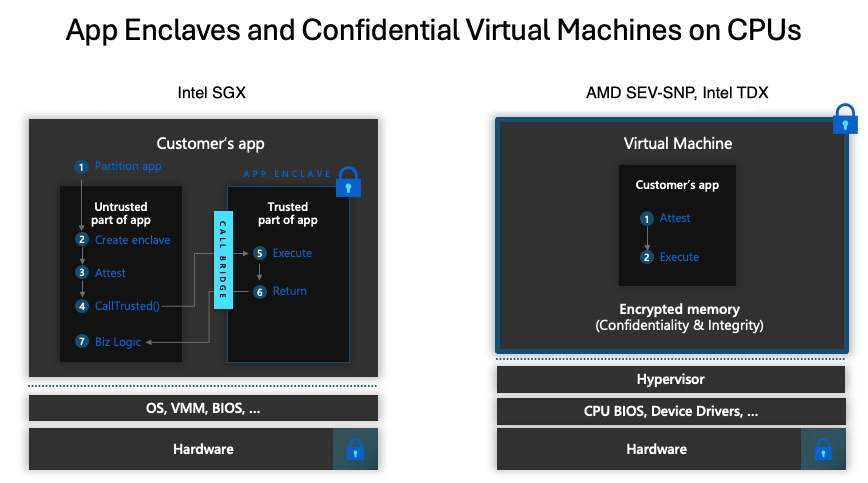
Despite these advances, hard problems persist. For instance, achieving high performance while enforcing strict integrity checks (such as those implemented via the Reverse Map Table in SEV-SNP) remains a delicate balancing act—ensuring that security enhancements do not impose unacceptable overhead in high-performance, multi-tenant data centers. Furthermore, the growing complexity of modern systems, especially those with NUMA architectures or heterogeneous device environments, poses challenges in uniformly maintaining a hardware root of trust. Issues such as securing device I/O paths, mitigating advanced side-channel attacks, and managing secure migration of VMs across untrusted hosts continue to be hard. While hardware-based trust solutions have come a long way over the past ten years, the quest to achieve an optimal blend of security, performance, and flexibility in an increasingly hostile and complex threat landscape remains an ongoing challenge.
Where the big money intersects this space is cloud compute, hardware-enforced confidential computing has become an indispensable tool for protecting sensitive workloads in multi-tenant environments. Technologies like AMD SEV‑SNP, Intel TDX, and Arm CCA each promise robust isolation by leveraging hardware mechanisms to encrypt memory, enforce integrity, and isolate virtual machines even in the presence of an untrusted hypervisor. However, while these solutions share the same overarching goal, they embody fundamentally different design philosophies and tradeoffs.
At the heart of these differences lies a tradeoff between security and performance, flexibility and complexity, as well as legacy compatibility versus future-proofing. For instance, AMD’s SEV‑SNP uses advanced techniques like the Reverse Map Table and multi-level guest privilege schemes to provide fine-grained integrity guarantees, which inevitably introduce additional overhead and management complexity. In contrast, Intel TDX offers a more abstracted approach to secure virtualization, which simplifies integration but can limit granular control. Meanwhile, Arm CCA, integrated directly into the ARMv9 ISA, emphasizes low overhead and tight integration at the cost of some of the flexibility seen in x86-based solutions.
And there is an open alternative. RISC‑V CoVE is a research‑driven initiative aimed at extending confidential computing to the open‑source RISC‑V ecosystem. Over the past decade, as hardware-based security became critical in data centers and cloud environments, proprietary technologies like Intel SGX and AMD SEV demonstrated the power of integrating security directly into the processor. Inspired by these efforts, the RISC‑V community began exploring ways to incorporate similar confidentiality and integrity features in a fully open and modular ISA. CoVE emerged as one of the early prototypes in this space, leveraging RISC‑V’s inherent flexibility to design hardware extensions that support secure enclaves, memory encryption, and integrity verification.
Technically, CoVE introduces mechanisms analogous to those found in proprietary systems but adapted for RISC‑V’s simpler architecture. This includes a dedicated memory encryption engine, hardware‑assisted isolation for virtual machines, and innovative techniques for tracking memory ownership—concepts similar to AMD’s Reverse Map Table, yet reimagined to suit an open‑source environment. The design also explores support for remote attestation and dynamic security policy enforcement within guest systems, offering a proof‑of‑concept that confidential virtualization is achievable without vendor lock‑in. While CoVE remains primarily in the research and prototyping phase, it highlights both the potential and the challenges of building robust hardware trust mechanisms on an open ISA, such as balancing performance overhead, ensuring seamless software integration, and achieving scalable adoption across diverse platforms.
CoVE could be the future. The economic landscape for confidential computing is heavily influenced by the licensing models adopted by key vendors—most notably AMD. If AMD’s licensing fees for its SEV‑SNP technology are perceived as too high by data centers and cloud service providers, it could create a significant cost barrier and incentivize investment in RISC‑V. Unlike proprietary solutions, RISC‑V offers a more open and flexible platform that—if coupled with effective confidential computing extensions—can dramatically lower both the entry and operational costs. This shift could spur a new wave of innovation as organizations seek to avoid high licensing costs, driving the development of open‑source confidential computing solutions that are not only cost‑effective but also adaptable to diverse workloads and deployment environments. In essence, the long‑term economics of hardware trust will depend on finding the right balance between robust security guarantees and accessible licensing terms, with the potential for RISC‑V to play a transformative role if traditional licensing models prove too burdensome.
Until a change in the market, Arm’s hardware protections remain critical. Arm Confidential Compute Architecture (CCA) represents a major evolution in secure computing for Arm-based systems. Introduced as an integral part of the Armv9 architecture, CCA builds on decades of lessons from TrustZone and other legacy security solutions to offer robust, hardware-enforced isolation for modern multi-tenant environments. At its core, CCA establishes a hardware root of trust by integrating memory encryption, secure boot, and remote attestation directly into the processor’s ISA—ensuring that sensitive workloads begin in a verified, trusted state. Unlike traditional approaches where security is largely managed in software, Arm CCA leverages dedicated security modules and encryption engines to protect the confidentiality and integrity of data, even when the hypervisor is untrusted. Designed to meet the demands of cloud, edge, and IoT applications, its architecture minimizes performance overhead while providing scalable, low-latency isolation across diverse devices. Over the past few years, as Arm processors have become ubiquitous in both mobile and server markets, industry collaboration has driven CCA’s maturation into a practical, next-generation solution for confidential computing that not only meets today’s threats but is also built to evolve alongside emerging challenges.
In the x86 space, Intel Trust Domain Extensions (TDX) represents Intel’s latest stride toward confidential computing in virtualized environments. Building on its long history of virtualization technology such as VT‑x, Intel introduced TDX to create “trusted domains” that isolate guest VMs even when the hypervisor is untrusted or compromised. Over the last few years, Intel has iteratively refined TDX to address evolving threats, integrating advanced memory encryption engines and robust access-control mechanisms directly into the CPU. TDX ensures that each virtual machine operates in a hardware‑enforced secure environment by encrypting guest memory with keys inaccessible to the host and by validating the integrity of critical VM state through specialized data structures and registers. Additionally, TDX supports remote attestation, allowing external parties to verify that a VM is running on a genuine, unmodified Intel platform with the latest security features. While aiming to minimize performance overhead, TDX also enforces strict isolation policies, ensuring that even if the hypervisor is breached, sensitive workloads remain protected. This evolution is crucial for cloud and data center applications, where trust in the underlying infrastructure is paramount.
AMD SEV‑SNP (Secure Encrypted Virtualization – Secure Nested Paging) is AMD’s most advanced solution for protecting virtual machines in environments where even the hypervisor is untrusted. Building on the foundation laid by earlier SEV technologies—which provided memory encryption (SEV) and extended protection of CPU register state (SEV‑ES)—SEV‑SNP adds critical integrity protections. It introduces hardware mechanisms like the Reverse Map Table (RMP) and new instructions (e.g., RMPUPDATE, PVALIDATE, and RMPADJUST) that enforce a strict one‑to‑one mapping between guest and system physical memory. These features ensure that any attempt to replay, remap, or alias memory pages is detected and blocked, thus safeguarding against sophisticated hypervisor-level attacks. Additionally, SEV‑SNP supports features such as VM Privilege Levels (VMPLs) that allow a guest to partition its own memory space for further internal security isolation. With robust remote attestation capabilities, SEV‑SNP enables cloud customers to verify that their VMs are running on genuine, unmodified AMD hardware with the latest security updates. This evolution in AMD’s confidential computing portfolio represents a significant leap forward, delivering both confidentiality and integrity protection essential for secure multi-tenant data centers and cloud environments.
Secure boot is the cornerstone of modern hardware trust—a process that ensures only verified and trusted code is executed right from the moment a system powers on. Think of it as the ultimate “ground zero” for security: if the foundation isn’t solid, everything built on top of it is at risk. In today’s era of distributed compute, from massive cloud data centers to edge devices, secure boot isn’t just an optional enhancement—it’s a necessity. It establishes a root of trust by validating the integrity of the system before any software is loaded, thereby underpinning all subsequent layers of defense. Without it, even the most sophisticated encryption and zero‑trust policies can fall prey to low‑level attacks that bypass software safeguards.
Different vendors have taken unique approaches to secure boot that reflect their broader security philosophies. For example, AMD’s SEV‑SNP integrates boot-time measurements with advanced memory encryption and integrity verification techniques, ensuring that only approved code is executed—albeit at the cost of added complexity and some performance overhead. Intel’s TDX takes a contrasting route by encapsulating entire virtual machines within “trusted domains,” streamlining the boot process at the expense of granular control. Meanwhile, Arm CCA embeds secure boot directly into the Armv9 ISA, delivering low‑overhead, highly efficient boot verification ideally suited for mobile, IoT, and edge scenarios. Risc-V CoVE is too early evaluate. Ultimately, regardless of the platform, secure boot provides that unbreakable starting point—ensuring that every subsequent layer of software security is built on a foundation that you can truly trust.
AMD’s approach to secure boot in SEV‑SNP extends the traditional concept by tightly integrating boot-time measurements with the VM launch process. Before a guest VM begins execution, its initial unencrypted image (containing boot code, for example) is measured and attested, ensuring that only trusted, approved code is executed. This process leverages a combination of hardware encryption, the Reverse Map Table (RMP), and remote attestation mechanisms to verify integrity. The tradeoff here is that while the process provides granular integrity guarantees even during live migration or in the presence of a malicious hypervisor, it introduces additional complexity and potential performance overhead during boot.
Intel TDX also supports secure boot, but its approach centers on establishing “trusted domains” where the entire virtual machine is launched within a protected environment. The boot process involves measuring and attesting to the initial state of the VM, ensuring that its critical data and code remain confidential throughout its lifecycle. Intel’s model abstracts much of the secure boot complexity from the guest OS by encapsulating the VM within a trusted domain. The advantage is a simpler integration for cloud environments with existing Intel infrastructure; however, this can limit fine‑grained control over the boot process compared to AMD SEV‑SNP, and it may require adjustments in legacy software to fully leverage the new protections.
In the Arm ecosystem, secure boot is built directly into the Armv9 ISA as part of a broader suite of security features. Arm CCA integrates secure boot with hardware‑assisted memory encryption and remote attestation, ensuring that each layer—from the bootloader up to the running OS—is authenticated before execution. This native integration minimizes overhead and offers a highly efficient secure boot process optimized for mobile, IoT, and cloud edge devices. However, because this approach is tightly coupled with the underlying hardware design, it can be less flexible when adapting to varied software requirements compared to more modular x86 solutions.
As a research‑driven initiative for the open‑source RISC‑V ecosystem, CoVE aims to replicate the robust features of proprietary solutions while maintaining the openness of the architecture. Its secure boot model is still evolving, designed to allow researchers to experiment with flexible, modular security extensions. While CoVE draws inspiration from both AMD and Intel approaches—such as measuring boot images and establishing a chain of trust—it also faces challenges common to research prototypes: ensuring compatibility with diverse implementations and achieving performance parity with more mature solutions. The tradeoffs here involve balancing experimental flexibility against the need for hardened, production‑grade security guarantees.
At the most basic level, physical security forms the bedrock of any robust confidential computing system—it’s the first line of defense that ensures all higher‑level security mechanisms have a trusted foundation. In modern architectures, this means integrating techniques like volume protection and physical unclonable functions (PUFs) to secure cryptographic keys and other sensitive data against physical tampering. For instance, AMD SEV‑SNP leverages its AMD Secure Processor (AMD‑SP) to generate and securely store memory encryption keys, often derived from PUFs, ensuring that these keys are intrinsically tied to the hardware and cannot be duplicated or extracted even with direct physical access. Similarly, Intel TDX relies on a hardware‑based root of trust where keys and attestation data are protected using secure boot and TPM-like mechanisms, making it essential for the underlying silicon to be physically secure. Arm CCA, embedded directly within the Armv9 ISA, also incorporates dedicated circuits for secure key generation (via PUFs) and enforces volume protection to guard against cold boot and side-channel attacks, all while maintaining low overhead for energy efficiency. In contrast, research initiatives like RISC‑V CoVE, which are developing confidential computing capabilities for open‑source platforms, must explicitly address these same physical security challenges from the ground up—balancing the need for openness and flexibility with rigorous hardware-based trust mechanisms. In every case, without stringent physical security—ranging from tamper‑resistant packaging to secure, hardware‑rooted key storage—no amount of software encryption or isolation can fully guarantee the confidentiality and integrity of sensitive workloads.
The evolution of hardware-based security—from early isolated execution environments to today’s advanced secure boot and confidential computing solutions—demonstrates that a robust hardware root of trust is indispensable. Whether it’s AMD SEV‑SNP’s intricate integrity mechanisms via the Reverse Map Table, Intel TDX’s trusted domains isolating entire virtual machines, Arm CCA’s deeply embedded secure boot within the Armv9 ISA, or the emerging flexibility of RISC‑V CoVE, each approach reflects a unique balance of security, performance, and complexity. These technologies not only secure the boot process and runtime environments but also integrate physical security measures such as volume protection and PUFs to safeguard cryptographic keys against tampering. As cloud and edge computing continue to expand, the quest to optimize this blend of hardware trust will be critical—driving future innovation and potentially reshaping the economics of confidential computing if proprietary licensing proves too burdensome.
If you want to get deeper into this area check out Confidential Computing.
Be the first to write a comment.